Checklist for securing remote desktop access in the cloud
If you are running Windows Server in the cloud, which you want to access via remote desktop (RDP) there are some basic security rules you need to follow. This is necessary, first and foremost because exposing RDP to the internet is “low hanging fruit” for hackers. We highly recommend taking the following ten steps.
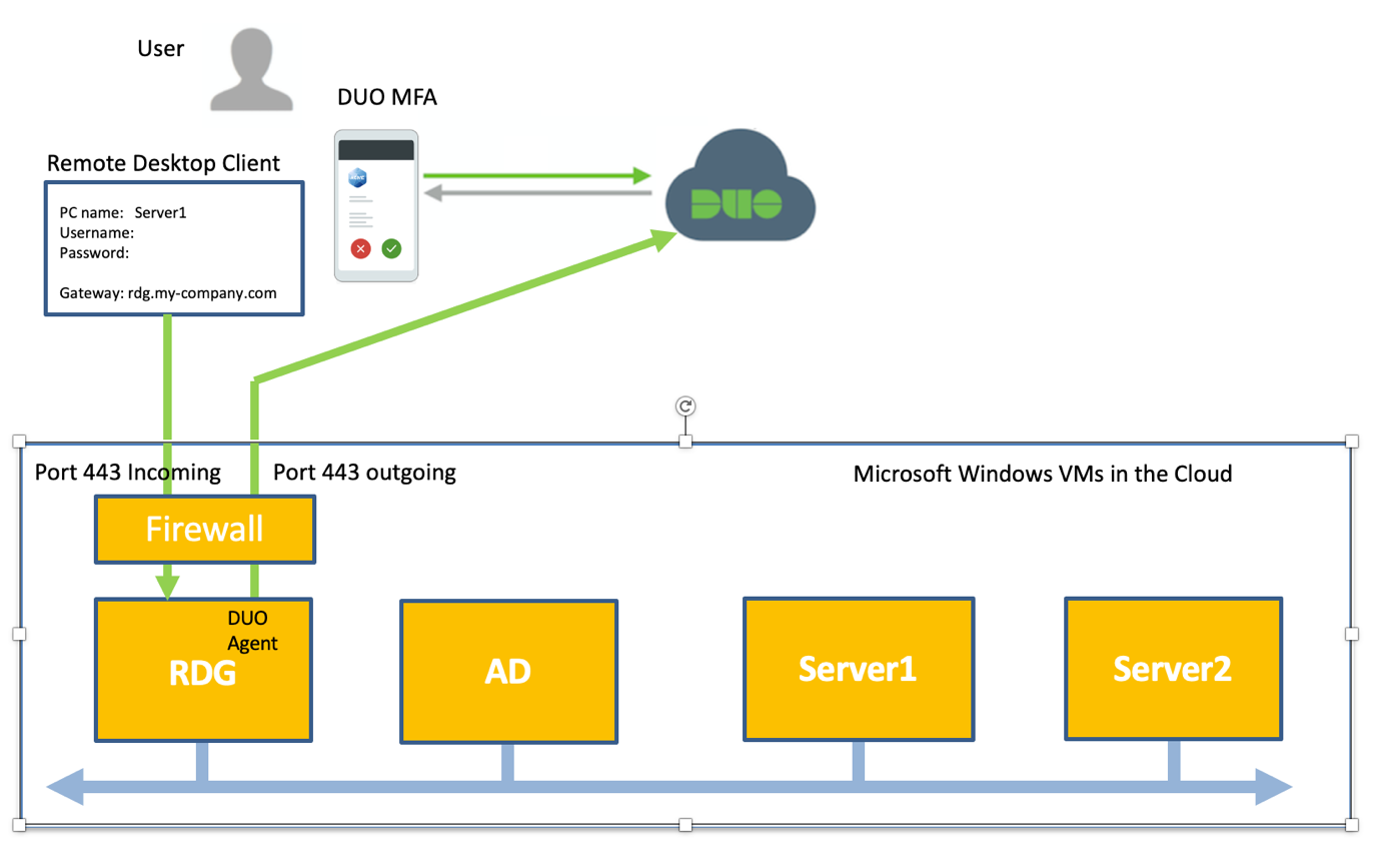
- Front the Windows Server(s) with a Remote Desktop Gateway (RDG). This acts as a proxy from HTTPS to RDP meaning that the user connections go over a secure, encrypted connection. Thisgateway should be the only way to access services resident on the enterprise Windows Servers.
- Configure the RDG to enforce multi-factor authentication (MFA) using e.g. Cisco DUO. When the user authenticates via the Remote Desktop Client, they are sent a push message to their mobile phone which has been pre-registered in the DUO cloud by an administrator. The user must approve the connection attempt via the DUO app installed on their phone. Since the user authentication must be confirmed in two independent places – the Active Directory (AD) and the DUO cloud, hacking attempts based on a stolen user name and password or brute-force attack are extremely difficult.
- Only allow port 443 incoming (ingress) from the internet to the RDG. All other non essential ports must be blocked.
- Add a DNS entry (‘A’ record) e.g. rdg.my-company.com which points to the RDG.
- Add a certificate e.g. self signed or from a trusted provider for your TLS encrypted HTTPS connection to the RDG.
- Ensure antimalware end-point protection e.g. Bitdefender is installed on the RDG and all Windows servers.
- Make sure your IT team or provider keeps the Remote Desktop Clients running in the user desktops updated with the latest code and patches.
- Make sure your IT team or provider keeps the RDG and Windows Servers patched on a regular basis. Microsoft releases patches at least every month.
- Implement strong password policies in the AD that lock users out of their machines after several unsuccessful attempts. Users will need to contact an administrator to reset the password.
- Use a Group Policy Setting to limit the number of system admins that can modify the RDG and RDPconfiguration.
IT Security Services by Safe Swiss Cloud
Protect your infrastructure from malware and ransomware. With security monitoring & 24/7 support.


Please Note:
You may use one of these HTML tags and attributes: <a href="" title=""> <abbr title=""> <acronym title=""> <b> <blockquote cite=""> <cite> <code> <del datetime=""> <em> <i> <q cite=""> <s> <strike> <strong>