The 5 most important considerations in going to “the cloud” explained. The fifth part of our series deals with the topic of Cost.
How can IT Decision Makers evaluate their Cloud Computing Options? #5 – Cost


The 5 most important considerations in going to “the cloud” explained. The fifth part of our series deals with the topic of Cost.
Author Prodosh Banerjee on 22 June 2023 Prodosh Banerjee's blog


Author Prodosh Banerjee on 20 June 2023 Prodosh Banerjee's blog
The 5 most important considerations in going to “the cloud” explained. The fourth part of our series deals with the topic of Choice.

Author Prodosh Banerjee on 15 June 2023 Prodosh Banerjee's blog
The 5 most important considerations in going to “the cloud” explained. The third part of our series deals with the topic of Compliance.

Author Prodosh Banerjee on 13 June 2023 Prodosh Banerjee's blog
The 5 most important considerations in going to “the cloud” explained. The second part of our series deals with the topic of Control.

Author Prodosh Banerjee on 12 June 2023 Prodosh Banerjee's blog
The 5 most important considerations in going to “the cloud” explained. The first part of our series deals with the topic of Convenience.
Author David Poole on 10 October 2022 David Poole's blog
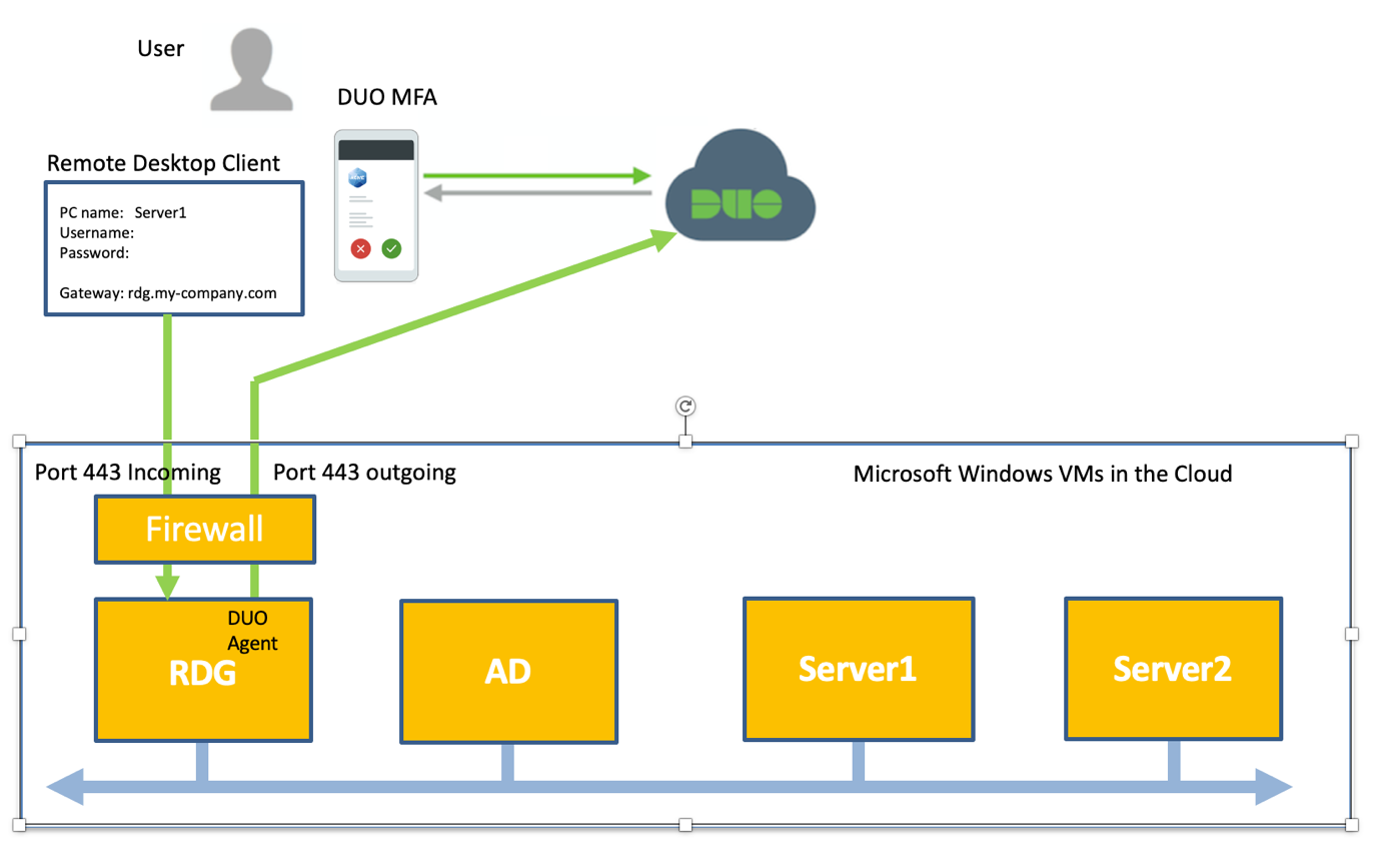
If you are running Windows Server in the cloud, which you want to access via remote desktop (RDP) there are some basic security rules you need to follow. This is necessary, first and foremost because exposing RDP to the internet is “low hanging fruit” for hackers. We highly recommend taking the following ten steps.

Author Prodosh Banerjee on 1 April 2022 Prodosh Banerjee's blog
IT security is a long and continuous process. But there are also quick measures you can implement immediately to improve your security and reduce the risk of ransomware infiltration. Here we present three of them.

Author Safe Swiss Cloud on 17 March 2022 Safe Swiss Cloud's blog
Safe Swiss Cloud’s new IT security services help customers improve their IT security and reduce their ransomware risk. The services can be seamlessly added to new as well as existing IT infrastructures. They help to identify risks early (SIEM, Active Directory Monitoring, End-Point Monitoring, Email, Firewall) and to recover from attacked environments (Ransomware Recovery). The regular monitoring of security services contributes significantly to the improvement of IT security. Safe Swiss Cloud therefore offers its IT security services with monitoring.
Author David Poole on 17 January 2022 David Poole's blog
Without the cloud it is very difficult to store and share the huge volumes of data needed for genome sequencing. Given the sensitivity of human genome data in terms of ownership and privacy, security and compliance are paramount.

Author Prodosh Banerjee on 17 May 2021 Prodosh Banerjee's blog
Organisations, whose functions are classified as “system relevant” by regulators (hospitals, banks etc.), suppliers to these organisations and those who provide important essential services, need to meet special criteria for business continuity: they need to be up and running again very quickly. In this blog post, we provide answers to the most important questions related to business continuity for cloud systems and services.
Author David Poole on 28 April 2021 David Poole's blog
You have heard of containers, but find them a bit of a mystery? Then this article is perfect for you. In it, we explain the concept and characteristics of containers. This helps to understand why containers are one of the big trends in IT.
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 1 year | Set by the GDPR Cookie Consent plugin, this cookie is used to record the user consent for the cookies in the "Analytics" category . |
| cookielawinfo-checkbox-marketing | 1 year | This cookie is set by the GDPR Cookie Consent plugin to store the user consent for the cookies in the category "Marketing". |
| cookielawinfo-checkbox-necessary | 1 year | Set by the GDPR Cookie Consent plugin, this cookie is used to record the user consent for the cookies in the "Necessary" category . |
| JSESSIONID | session | Used for Cross Site Request Forgery (CSRF) protection |
| sdsc | session | Signed data service context cookie used for database routing to ensure consistency across all databases when a change is made. Used to ensure that user-inputted content is immediately available to the submitting user upon submission |
| viewed_cookie_policy | 1 year | The cookie is set by the GDPR Cookie Consent plugin to store whether or not the user has consented to the use of cookies. It does not store any personal data. |
| Cookie | Duration | Description |
|---|---|---|
| _ga | 2 years | The _ga cookie, installed by Google Analytics, calculates visitor, session and campaign data and also keeps track of site usage for the site's analytics report. The cookie stores information anonymously and assigns a randomly generated number to recognize unique visitors. |
| _ga_D83559EP8M | 2 years | This cookie is installed by Google Analytics. |
| browser_id | 5 years | This cookie is used for identifying the visitor browser on re-visit to the website. |
| split | 1 month | This cookie is used to evaluate the changes to the website by checking which multivariate test the user takes part in. |
| Cookie | Duration | Description |
|---|---|---|
| bcookie | 1 year | Browser Identifier cookie to uniquely indentify devices accessing LinkedIn to detect abust on the platform and diagnostic purposes |
| bscookie | 1 year | Used for remembering that a logged in user is verified by two factor authentication |
| lang | session | Used to remember a user's language setting to ensure LinkedIn.com displays in the language selected by the user in their settings |
| li_gc | 6 months | Used to store consent of guests regarding the use of cookies for non-essential purposes |
| li_mc | 6 months | Used as a temporary cache to avoid database lookups for a member's consent for use of non-essential cookies and used for having consent information on the client side to enforce consent on the client side |
| lidc | 24 hours | To facilitate data center selection |